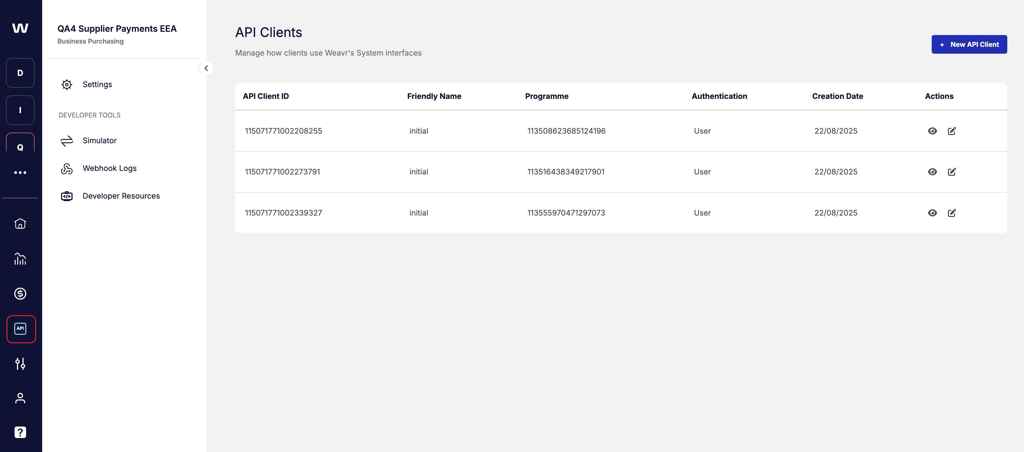
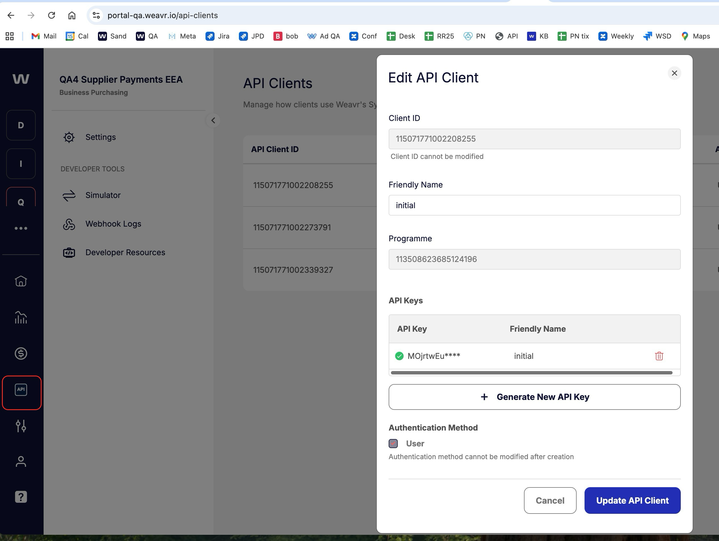
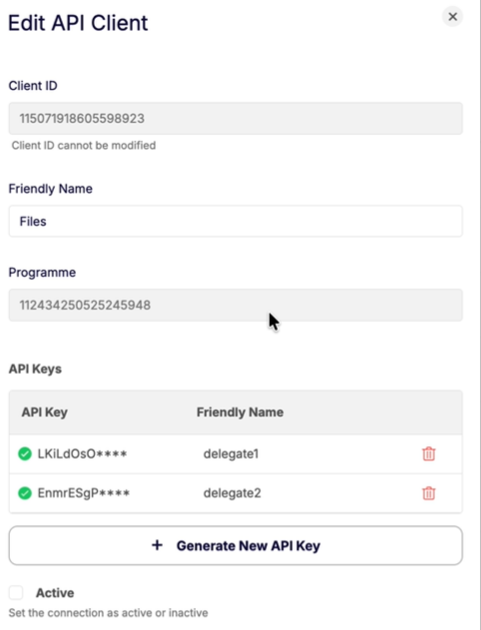
Manage spend limits on debit-mode cards in the user's own currency
Weavr is enhancing its debit card offering by introducing the ability to configure spend limits in a secondary currency—different from the card's assigned currency, known as the userCurrency.
Cardholders will be able to view their card balance and set spend limits in their designated userCurrency, providing greater flexibility and transparency in managing expenses.
Note that once a card is created, its assigned userCurrency cannot be changed.
Key points
JPY, BGN, CZK, DKK, HUF, PLN, RON, SEK, CHF, ISK, NOK, TRY, AUD, BRL, CAD, CNY, HKD, IDR, ILS, INR, KRW, MXN, MYR, NZD, PHP, SGD, THB, ZAR
Consider a UK-based company with employees located in Sweden. If the company enables SEK (Swedish Krona) as a userCurrency, it can assign this secondary currency when issuing cards to Swedish employees. It’s important to note that specifying a userCurrency does not alter the underlying card’s issuing currency with our banking partners. The card’s primary currency remains unchanged, and all card statements will continue to be reported in the original issuing currency.
API details
-
POST /managed_cards
-
GET /managed_cards/{id}
-
GET /managed_cards
-
POST /managed_cards/{id}/spend_rules
-
PATCH /managed_cards/{id}/spend_rules
-
GET /managed_cards/{id}statement
Further details are available in our product documentation here
Webhook details
via API
We have added a new field, detailsDeliveryTrackingUrl, to the multi and back-office Get Card API endpoints. When available, this field provides a direct link to the courier's tracking information page for the physical card delivery, allowing you to monitor the delivery status of a physical card in real time.
via Embedder portal
Where possible, the same detail has been added to the embedder portal, making it easier to access the courier's tracking information with a single click, that takes you directly to the courier’s tracking page, making it easier to monitor delivery status and updates in real time.
Functionality to set custom start date for a spend limit interval
We’ve enhanced our spend rule creation capabilities to give you more flexibility when setting spending limits for physical and virtual debit mode cards.
Card owners (corporate root or authorised users) can now customise the start date for spend limits based on the selected interval—whether it's weekly, monthly, quarterly, or yearly.
For example, you can now set a yearly spend limit that starts on May 1 2025 and ends on May 1 2026.
This gives you more control in aligning spend limits with your financial planning cycles.
This update is on multi and back-office.
API details
-
POST /multi/managed_cards/{id}/spend_rules
-
PATCH /multi/managed_cards/{id}/spend_rules
-
PATCH /multi/bulks/managed_cards/_id_/spend_rules
-
POST multi/backoffice/managed_cards/{id}/spend_rules
-
PATCH /multi/backoffice/managed_cards/{id}/spend_rules
-
PATCH /multi/backoffice/bulks/managed_cards/_id_/spend_rules
AuthorisationCategory field in APIs and Authorisation Webhooks
We’ve introduced a new field called AuthorisationCategory in our card statement APIs and authorisation webhooks. This field helps you distinguish whether a card authorisation is a pre-authorisation or a final authorisation. AuthorisationCategory will support
-
PRE_AUTH Indicates a pre-authorisation, commonly used for reserving funds (e.g., hotels, rentals).
-
FINAL_AUTH Indicates a final authorisation, typically representing the actual transaction amount.
This new field allows for better control and visibility over transaction flows. You can:
-
Accurately track the lifecycle of a payment
-
Differentiate between temporary holds and completed payments
-
Improve reconciliation and customer communication
API details
Webhooks
/managed_cards_authorisations_watch
More efficient statement retrieval
We have made improvements to our statement retrieval process (for cards and accounts). Previously, due to API limitations, statement data was provided in pages of 100 items, sometimes requiring multiple requests for complete information.
We have now increased the maximum number of items per page to 500. This enhancement will streamline the process of retrieving your statement data.
To benefit from the increased limits, specify your desired limit in the limit parameter when making a GET request to the statement API. Or contact your account manager to configure an appropriate default limit.
Key Points
If no specific limit is requested, the system will default to 100 items or a limit that has been agreed with your account manager (maximum of 500) .
If the statements request includes a period before April 1, 2025 , the maximum limit of 100 will still apply.
If the limit specified in the API request is higher than the configured limit , the limit will internally fall back to the configured limit.
API Details
We believe these updates will significantly improve your experience in accessing and managing your card and account statements.