Version 3.51.1
Service Updates
Physical payment card fulfilment centre in EU
We are glad to announce the availability of card printing and logistics based in the EU.
This will help reduce delivery times for EU-based cardholders compared to the main fulfilment centre in the UK.
If you have queries about card printing and delivery for your programme, including pricing, please contact your Account Manager, or open a support ticket, and we’ll be glad to assist.
Digital signature in KYB forms
A reminder to Embedders that digital signatures on PDFs (such as via Docusign or Pandadoc) are acceptable for completion of various forms in the KYB process such as UBO declarations.
If you have any queries about the KYB process and documents/steps, please contact your Account Manager or open a support ticket and we’ll be glad to assist.
Product Updates
KYB: Proof of ID document expiry process changes
We are making a number of changes in this release to how we handle expiry of proof of ID (PoI) documents in KYC and KYB. Expiry refers to the “valid until” or “expires” date shown on the form of ID (such as a passport or national ID card).
The key points are as follows:
-
Any Consumer with an expired PoI document will be restricted from transacting, after a reasonable time to react to support requests, until they return their KYC to good standing by providing a replacement/valid ID document (all else being in good standing).
-
Any Corporate’s KYB good standing depends on the individual PoI documents being valid (not expired) for the Root User (/appointee), plus ALL of Ultimate Beneficial Owners (UBOs). All of the Corporate’s accounts/cards will be restricted from transacting if any of the required IDs are deemed to be out of date after attempts to alert the stakeholders, until brought back into good standing.
-
In any actual restriction action Weavr will send a webhook and notification email as well as proactive support team engagement.
-
The Embedder has the primary responsibility to communicate with End Customers and their representatives/stakeholders in advance of PoI expiry and in the event of documents having expired. Embedders' systems should provide one or more advance warnings to the relevant end customer contacts.
-
Weavr will now send webhooks to the Embedder’s endpoint for every soon-to-expire PoI 30 days before expiry, 10 days before, and on the day of expiry. In addition a final warning is sent 10 days after the day of expiry. Embedders should use these webhooks to construct the relevant notifications for End Customer stakeholders.
-
In addition to the above webhooks, Weavr will send emails directly to the affected Root User (or non-director Root User plus director appointing them). The email content is as follows and can be customised by the Embedder for their programme, on request via support ticket:
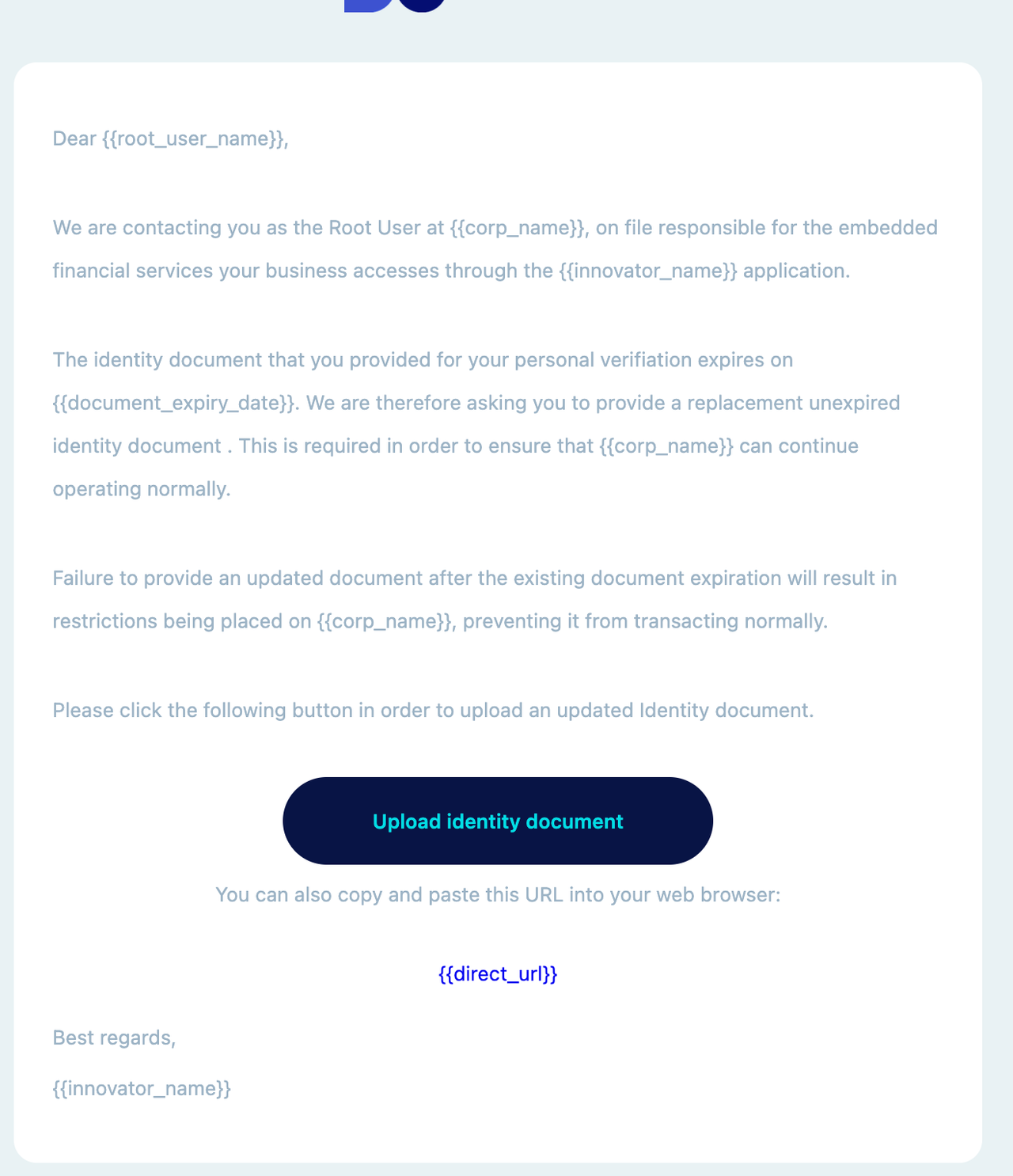
-
The above email will be sent 30/10/0 days before as well as 10 days after the ID document expiry date.
-
The 30/10 days before and 10 days after expiry timeframes are configurable per Embedder programme: please contact Weavr if you wish to make changes in this regard.
-
Please note that any accounts currently affected by having one or more PoI documents already expired at the go-live date of this release, will already be subject to compliance case management with Embedder support teams. Any soon-to-expire cases after the go-live date will begin receiving reminders immediately.
Please read the full article on Proof of ID expiry to find out more (requires Weavr Support Portal login).
Sends and OWTs as bulk operations
As announced in the last Release Note, we have introduced a capability to group multiple individual API-based actions into a batch of bulk operations; that are then executed and managed through the Bulk Process. This new feature is available to try out, on request (via support ticket or your account manager).
We have now added the following actions as bulk operations endpoints:
-
POST bulks/sends- Create Sends in bulk. -
POST bulks/outgoing_wire_transfers- Create OWTs in bulk.
To complete these operations, a transaction confirmation challenge must also be completed, and so we have updated our Bulk Process documentation to describe this.
The previous endpoints that specifically served bulk Sends and bulk OWTs will be marked as deprecated, since these operations can now be managed as part of the standardised Bulk Process.
Cancel OWTs in state PENDING_CHALLENGE
Previously, an Outgoing Wire Transfer (OWT) could be cancelled only if it was a scheduled (i.e. future-dated) transaction, at any time before the execution time. This is done by selecting the scheduled OWT transaction ID and cancelling it, optionally adding a cancellation reason.
With the updated POST /outgoing_wire_transfers/bulk/cancel endpoint, an OWT can be cancelled while it is still in the state PENDING_CHALLENGE, i.e. before the completion of the SCA challenge.
A single OWT or batch of OWTs can be cancelled in this way.
Therefore, Embedders can now add functionality to their OWT UX flow to offer account holders the ability to cancel an OWT at this stage, e.g. to go back, change details of the OWT, and start again.
Shared fees for Send transactions
Currently, it is possible to configure and test various transaction fees in the Embedder Portal within the Sandbox environment. These fees are subject to checks and approval before they are applied in a live programme.
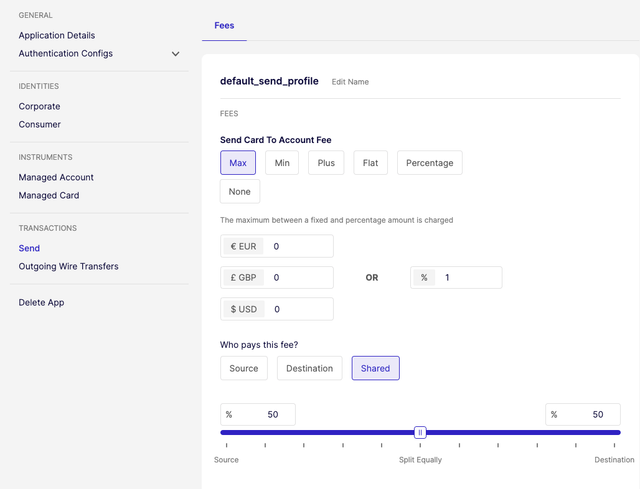
With this release we are adding a new fee mechanism for Sends (i.e. e-money payments between two different Identities' Managed Accounts under the same programme). Instead of a fee for a Send only being charged to the sender (the source account), some or all of the fee can now be shifted to the recipient (destination account).
New configuration is available in the Sandbox Portal to set up this kind of split/shared fees on Sends:
- Charge full fee to the source account,
- Charge full fee to the destination account, or
- Split fee between the source and the destination account: with the split being 50/50, or any percentage weighting you chose.
Fees that have been charged to End Customers in this way will be shown in their statements and transaction history - now, for both source and destination accounts.
Fees on Send transactions are specified on a Send Profile. The Send Profile is specified in the API call to initiate the transaction: therefore it is possible to have different Send Profiles for different fee approaches, and select the right one at the time of a transaction.
Embedders wishing to apply fee changes to a live programme should raise a change request via a support ticket.
Updating card spend rules as a bulk operation
As announced in the last Release Note, one of the bulk operations to be included in the launch of the Bulk Process was the ability to bulk update spend rules across Managed Cards.
The Bulk Process, and specifically the ability to bulk update spend rules across Managed Cards, is now also available in the Back Office API.
The endpoint introduced is POST bulks/managed_cards/_id_/spend_rules.
Please contact Weavr support for guidance in testing out the new bulk operations features during this Beta phase.
Creation and delivery details for physical cards in Embedder Portal
We have improved the Managed Cards detailed view in the Embedder Portal for programme administrators and support teams. This update provides more details about physical payment cards, which are set up by first creating a virtual card and then upgrading to physical:
- A timestamp indicating when the Managed Card was upgraded to a physical card,
- The manufacturing state of the card, and
- Delivery tracking details, if available.
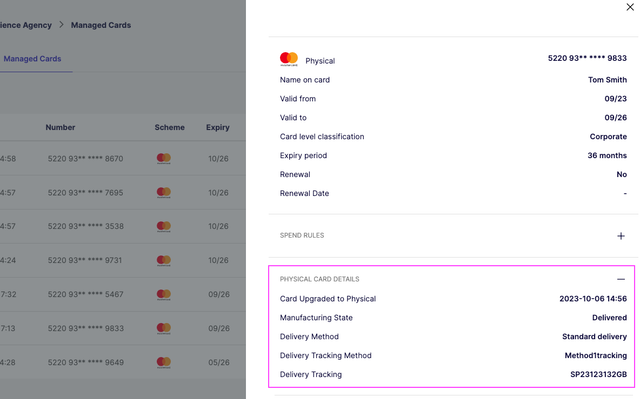
The manufacturing states of a Card can be:
REQUESTED: The upgrade of the card to physical has been requested.SENT_FOR_FULFILLMENT: The card has been sent for printing.DISPATCHED: The card has been manufactured and dispatched.DELIVERED: The card has been received and activated by the recipient.
Delivery tracking details are added when the manufacturing state is either DISPATCHED or DELIVERED.
Reminder: A Managed Card can be upgraded to a physical card by calling the Multi API endpoint POST /managed_cards/{id}/physical. For more information on setting up physical cards, please refer to our API guides.
Indication of which API key is used for webhook signing
In previous release notes we noted how we are strengthening the mechanism of signing webhooks. Webhooks are signed using the Primary API Key of a programme. This key is now highlighted in the API Credentials list in the Embedder Portal:
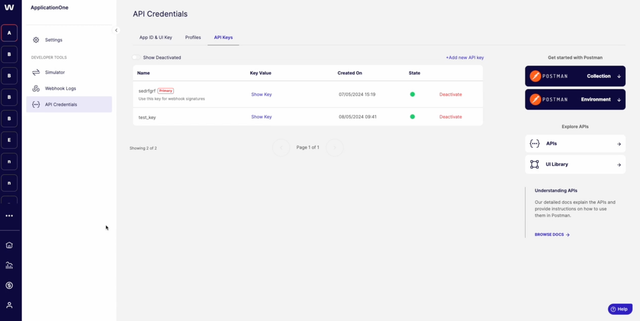
The key marked as Primary is the one that has been active for longest. This applies to both Sandbox and live applications.
We recommend all Embedders move over to the new webhook signing / validation mechanism as soon as convenient.
Additional endpoints now supporting idempotency
As mentioned in previous Release Notes, we are extending the list of endpoints in the Multi API which can be called idempotently. This can be achieved by including the idempotency-ref header in the requests.
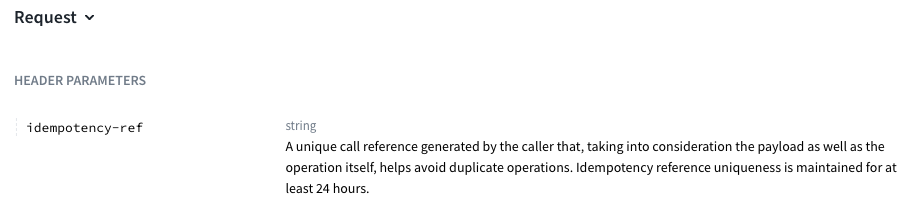
In this release, the following Multi API endpoints can (optionally) be called idempotently:
-
POST/corporatesto create a Corporate Identity -
POST /consumersto create an Consumer Identity -
POST /multi/users/inviteto send a user invite -
POST users/{user_id}/invite/consumeto consume an invitation previously sent to the user -
PATCH /users/{user_id}to update details of a User -
POST users/verification/email/sendto send an email verification code to an Authorised User
Further information on idempotency is provided in our API Docs here.
SSO for Embedder Portal
We are now offering Single Sign-On (SSO) for the Embedder Portal on a Beta basis. Users will be able to log in to the portal using their company-provided authentication e.g. Google Workspace or Microsoft account.
This provides enhanced security and convenience for controlling access and adding/removing users from your organisation to work with the portal.
If you would like to participate in this Beta, please contact Weavr (via support ticket or your account manager).
Partner Notice
Security reminder from Twilio Authy
Please note that Twilio has recently announced an important update for Authy.
If your programme uses Authy for SCA or other 2FA please help communicate this to your end users with a reminder to update their app as soon as possible.

 Option to use biometrics as the primary/default Step Up login with a fallback to SMS OTP.
Option to use biometrics as the primary/default Step Up login with a fallback to SMS OTP. Option to use biometrics as well as - or instead of - SMS OTP when confirming outgoing (non-card) payments.
Option to use biometrics as well as - or instead of - SMS OTP when confirming outgoing (non-card) payments. Option to use biometrics as well as - or instead of - SMS OTP when confirming outgoing (non-card) payments.
Option to use biometrics as well as - or instead of - SMS OTP when confirming outgoing (non-card) payments. The new Data Insights tab in the card Settlements dashboard allows Embedder Portal staff users to review End Customer financial activity in the currency of the card or account instrument.
The new Data Insights tab in the card Settlements dashboard allows Embedder Portal staff users to review End Customer financial activity in the currency of the card or account instrument. Embedder Portal staff users can review individual Send transactions with additional details displayed about the source and destination accounts.
Embedder Portal staff users can review individual Send transactions with additional details displayed about the source and destination accounts.
